Ticket #685 (closed task: fixed)
SSL certificate about to expire?
| Reported by: | sam | Owned by: | chris |
|---|---|---|---|
| Priority: | critical | Milestone: | Maintenance |
| Component: | Live server | Keywords: | SSL |
| Cc: | sam | Estimated Number of Hours: | 0.0 |
| Add Hours to Ticket: | 0 | Billable?: | yes |
| Total Hours: | 3.65 |
Description
Hi Chris this dropped into my inbox this morning.
Can you tell from the following if it's a certificate we still use? Does it need to be renewed?
Thanks
Sam
---
Hello,
This mail is to inform you that your certificate SSL Standard (*.transitionnetwork.org) expires today, on 2014-01-24 00:59.
Warning: for Pro and Business certificates, web browsers have increased security. It can now take up to several weeks, and so we strongly recommend that you perform the operation as soon as possible.
If you would like to keep your certificate, we recommend renewing it today. For this you must launch the renewal process from the following page: https://www.gandi.net/admin/ssl/renew/26873
If you do not want to keep your certificate, then no further action is necessary on your part. It will be automatically revoked by our services and rendered useless.
Attachments
Change History
comment:1 Changed 3 years ago by chris
- Add Hours to Ticket changed from 0.0 to 0.1
- Total Hours changed from 0.0 to 0.1
comment:2 Changed 3 years ago by chris
- Cc sam added
- Add Hours to Ticket changed from 0.0 to 0.25
- Status changed from new to accepted
- Owner changed from Chris to chris
- Total Hours changed from 0.1 to 0.35
Following ticket:475, generating a new CSR on penguin:
sudo -i cd /etc/ssl/transitionnetwork.org mkdir 2014 chmod 700 2014 cd 2014 openssl req -nodes -newkey rsa:2048 -keyout transitionnetwork.org.key -out transitionnetwork.org.csr Generating a 2048 bit RSA private key ...........+++ .............................+++ writing new private key to 'transitionnetwork.org.key' ----- You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [AU]: State or Province Name (full name) [Some-State]: Locality Name (eg, city) []: Organization Name (eg, company) [Internet Widgits Pty Ltd]: Organizational Unit Name (eg, section) []: Common Name (e.g. server FQDN or YOUR name) []:*.transitionnetwork.org Email Address []: Please enter the following 'extra' attributes to be sent with your certificate request A challenge password []: An optional company name []:
Due to the time constraints I have placed the order for the new cert, once again so sorry to have missed this yesterday.
comment:3 Changed 3 years ago by chris
- Add Hours to Ticket changed from 0.0 to 0.1
- Total Hours changed from 0.35 to 0.45
Sam, the reason I didn't get a email about this ticket yesterday is because it was assigned to Chris not chris -- the trac usernames are case sensitive, note the change above, ticket:685#comment:2
- Owner changed from Chris to chris
comment:4 Changed 3 years ago by chris
- Add Hours to Ticket changed from 0.0 to 0.1
- Total Hours changed from 0.45 to 0.55
Sam is your email account working OK or is your email address in Trac incorrect? I got a bounce back from the last comment on this ticket:
<sam.rossiter@transitionnetwork.org>: host mx1.spamfiltering.com[212.113.130.124] said: 550 no mailbox by that name is currently available (in reply to RCPT TO command)
Still waiting the the cert from gandi / Comodo, it should be through in an hour or two, hopefully sooner.
comment:5 Changed 3 years ago by sam
Hi Chris. Thanks for getting on the case with this.
I don't seem to get any email from trac at all.. The email is correct though.
Thanks
Sam
comment:6 Changed 3 years ago by chris
- Add Hours to Ticket changed from 0.0 to 0.6
- Total Hours changed from 0.55 to 1.15
It's finally come through! Saved as transitionnetwork.org.crt
Following ticket:475, generate a chained .pem file:
cd /etc/ssl/transitionnetwork.org/2014 cat transitionnetwork.org.crt > transitionnetwork.org.pem cat transitionnetwork.org.key >> transitionnetwork.org.pem
Generate the gandi.pem file:
wget http://crt.gandi.net/GandiStandardSSLCA.crt -O GandiStandardSSLCA.crt wget http://crt.usertrust.com/UTNAddTrustServer_CA.crt -O UTNAddTrustServer_CA.crt wget http://crt.usertrust.com/AddTrustExternalCARoot.crt -O AddTrustExternalCARoot.crt openssl x509 -inform DER -in GandiStandardSSLCA.crt -out GandiStandardSSLCA.pem openssl x509 -inform DER -in AddTrustExternalCARoot.crt -out AddTrustExternalCARoot.pem openssl x509 -inform DER -in UTNAddTrustServer_CA.crt -out UTNAddTrustServer_CA.pem cat GandiStandardSSLCA.pem > gandi.pem cat AddTrustExternalCARoot.pem >> gandi.pem cat UTNAddTrustServer_CA.pem >> gandi.pem
Generate the chained pem file for nginx (CHECK FOR WHITESPACE PROBLEMS!):
cat transitionnetwork.org.crt > transitionnetwork.org.chained.pem cat GandiStandardSSLCA.pem >> transitionnetwork.org.chained.pem cat UTNAddTrustServer_CA.pem >> transitionnetwork.org.chained.pem cat AddTrustExternalCARoot.pem >> transitionnetwork.org.chained.pem
Move into place on wiki:PenguinServer:
cd /etc/ssl/transitionnetwork.org mv transitionnetwork.org* 2013/ mv 2014/* .
Test and restart Nginx:
/etc/init.d/nginx configtest [ ok ] Testing nginx configuration:. /etc/init.d/nginx restart [ ok ] Restarting nginx: nginx.
Enable root ssh on wiki:PuffinServer, edit /etc/ssh/sshd_config and change:
PermitRootLogin yes # PermitRootLogin no
Restart:
/etc/init.d/ssh restart
sudo -i cd /etc/ssl/transitionnetwork.org mkdir 2014
rsync -av transitionnetwork.org.* puffin:/etc/ssl/transitionnetwork.org/2014/
cd /etc/ssl/transitionnetwork.org mkdir 2013 mv transitionnetwork.org* 2013/ mv 2014/* . chmod 600 transitionnetwork.org.* /etc/init.d/nginx configtest nginx: the configuration file /etc/nginx/nginx.conf syntax is ok nginx: configuration file /etc/nginx/nginx.conf test is successful /etc/init.d/nginx restart
Switch off root ssh access on wiki:PuffinServer, edit /etc/init.d/sshd_config:
PermitRootLogin no #PermitRootLogin yes
And restart:
/etc/init.d/ssh restart
Restart postfix on wiki:PuffinServer:
/etc/init.d/postfix restart [....] Stopping Postfix Mail Transport Agent: postfix/usr/sbin/postconf: warning: /etc/postfix/main.cf: unused parameter: smtpd_tls_cipherlist=EDH:!EXP:!LOW . ok [....] Starting Postfix Mail Transport Agent: postfixpostconf: warning: /etc/postfix/main.cf: unused parameter: smtpd_tls_cipherlist=EDH:!EXP:!LOW postconf: warning: /etc/postfix/main.cf: unused parameter: smtpd_tls_cipherlist=EDH:!EXP:!LOW postconf: warning: /etc/postfix/main.cf: unused parameter: smtpd_tls_cipherlist=EDH:!EXP:!LOW postconf: warning: /etc/postfix/main.cf: unused parameter: smtpd_tls_cipherlist=EDH:!EXP:!LOW postconf: warning: /etc/postfix/main.cf: unused parameter: smtpd_tls_cipherlist=EDH:!EXP:!LOW postconf: warning: /etc/postfix/main.cf: unused parameter: smtpd_tls_cipherlist=EDH:!EXP:!LOW /usr/sbin/postconf: warning: /etc/postfix/main.cf: unused parameter: smtpd_tls_cipherlist=EDH:!EXP:!LOW /usr/sbin/postconf: warning: /etc/postfix/main.cf: unused parameter: smtpd_tls_cipherlist=EDH:!EXP:!LOW /usr/sbin/postconf: warning: /etc/postfix/main.cf: unused parameter: smtpd_tls_cipherlist=EDH:!EXP:!LOW /usr/sbin/postconf: warning: /etc/postfix/main.cf: unused parameter: smtpd_tls_cipherlist=EDH:!EXP:!LOW /usr/sbin/postconf: warning: /etc/postfix/main.cf: unused parameter: smtpd_tls_cipherlist=EDH:!EXP:!LOW /usr/sbin/postconf: warning: /etc/postfix/main.cf: unused parameter: smtpd_tls_cipherlist=EDH:!EXP:!LOW /usr/sbin/postconf: warning: /etc/postfix/main.cf: unused parameter: smtpd_tls_cipherlist=EDH:!EXP:!LOW /usr/sbin/postconf: warning: /etc/postfix/main.cf: unused parameter: smtpd_tls_cipherlist=EDH:!EXP:!LOW /usr/sbin/postconf: warning: /etc/postfix/main.cf: unused parameter: smtpd_tls_cipherlist=EDH:!EXP:!LOW /usr/sbin/postconf: warning: /etc/postfix/main.cf: unused parameter: smtpd_tls_cipherlist=EDH:!EXP:!LOW /usr/sbin/postconf: warning: /etc/postfix/main.cf: unused parameter: smtpd_tls_cipherlist=EDH:!EXP:!LOW /usr/sbin/postconf: warning: /etc/postfix/main.cf: unused parameter: smtpd_tls_cipherlist=EDH:!EXP:!LOW /usr/sbin/postconf: warning: /etc/postfix/main.cf: unused parameter: smtpd_tls_cipherlist=EDH:!EXP:!LOW /usr/sbin/postconf: warning: /etc/postfix/main.cf: unused parameter: smtpd_tls_cipherlist=EDH:!EXP:!LOW /usr/sbin/postconf: warning: /etc/postfix/main.cf: unused parameter: smtpd_tls_cipherlist=EDH:!EXP:!LOW /usr/sbin/postconf: warning: /etc/postfix/main.cf: unused parameter: smtpd_tls_cipherlist=EDH:!EXP:!LOW . ok
Some config needs fixing there...
sudo -i cd /etc/ssl/transitionnetwork.org/ mkdir 2013 ; chmod 700 2013 mkdir 2014 ; chmod 700 2014
Edit /etc/ssh/sshd_config and change:
#PermitRootLogin no PermitRootLogin yes
Restart:
/etc/init.d/ssh restart [ ok ] Restarting OpenBSD Secure Shell server: sshd.
rsync -av transitionnetwork.org.* parrot:/etc/ssl/transitionnetwork.org/2014/ sending incremental file list transitionnetwork.org.chained.pem transitionnetwork.org.crt transitionnetwork.org.csr transitionnetwork.org.key transitionnetwork.org.pem sent 14848 bytes received 107 bytes 29910.00 bytes/sec total size is 14521 speedup is 0.97
cd /etc/ssl/transitionnetwork.org mv transitionnetwork.org.* 2013/ mv 2014/* . chmod 600 transitionnetwork.org.* apache2ctl configtest Syntax OK /etc/init.d/apache2 restart [ ok ] Restarting web server: apache2 ... waiting .
Changed 3 years ago by chris
Changed 3 years ago by chris
Changed 3 years ago by chris
comment:7 follow-up: ↓ 8 Changed 3 years ago by chris
- Add Hours to Ticket changed from 0.0 to 0.45
- Total Hours changed from 1.15 to 1.6
Disallow root ssh on wiki:ParrotServer again, edit /etc/ssh/sshd_config and change:
PermitRootLogin no #PermitRootLogin yes
Restart:
/etc/init.d/ssh restart [ ok ] Restarting OpenBSD Secure Shell server: sshd.
Test site and document the new cert, updating wiki:SecurityInfo and http://wiki.transitionnetwork.org/Security
Test results for https://transitionnetwork.org/ via https://www.ssllabs.com/ssltest/analyze.html?d=transitionnetwork.org
Test results for https://penguin.transitionnetwork.org/ via https://www.ssllabs.com/ssltest/analyze.html?d=penguin.transitionnetwork.org&s=81.95.52.111
Test results for https://parrot.transitionnetwork.org/ via https://www.ssllabs.com/ssltest/analyze.html?d=parrot.transitionnetwork.org
The Transition Network Zone file has been updated to remove the comodo subdomain, this is the latest version:
* 3600 IN A 81.95.52.103 *.newdev 3600 IN A 81.95.52.103 *.parrot 3600 IN A 81.95.52.43 2010.archive 3600 IN A 81.95.52.111 2011.archive 3600 IN A 81.95.52.111 @ 3600 IN A 81.95.52.103 lists 3600 IN A 212.113.133.235 mail 3600 IN A 212.113.133.235 newdev 3600 IN A 81.95.52.103 parrot 3600 IN A 81.95.52.43 penguin 3600 IN A 81.95.52.111 power 3600 IN A 81.95.52.111 puffin 3600 IN A 81.95.52.103 redirects 3600 IN A 81.95.52.111 static 3600 IN A 81.95.52.111 stats 3600 IN A 81.95.52.111 tech 3600 IN A 81.95.52.111 totnes 3600 IN A 81.95.52.111 trac 3600 IN A 81.95.52.111 wagn 3600 IN A 81.95.52.111 wiki 3600 IN A 81.95.52.111 www 3600 IN A 81.95.52.103 www.penguin 3600 IN A 81.95.52.111 www.totnes 3600 IN A 81.95.52.111 www.wiki 3600 IN A 81.95.52.111 @ 3600 IN MX 0 mx1.spamfiltering.com. @ 3600 IN MX 5 mx2.spamfiltering.com. tech 10800 IN MX 10 mx.webarch.net.
TODO:
- Enable Forward Secrecy on wiki:ParrotServer
- Update wiki:SecurityInfo
- Update http://wiki.transitionnetwork.org/Security
- Update wiki:DomainNames
- Fix Sam's Trac email address
comment:8 in reply to: ↑ 7 Changed 3 years ago by chris
- Add Hours to Ticket changed from 0.0 to 1.6
- Total Hours changed from 1.6 to 3.2
Replying to chris:
TODO:
- Enable Forward Secrecy on wiki:ParrotServer
Following the suggestions at https://github.com/t2d/wasuptls edited /etc/apache2/mods-available/ssl.conf
#SSLCipherSuite HIGH:MEDIUM:!aNULL:!MD5 SSLCipherSuite ECDH+AESGCM:DH+AESGCM:ECDH+AES256:DH+AES256:ECDH+AES128:DH+AES:ECDH+3DES:DH+3DES:RSA+AES:RSA+3DES:!ADH:!AECDH:!MD5:!DSS:!aNULL SSLHonorCipherOrder on SSLCompression off
Edited the apache templates in /root/webarch/conf/ and /usr/local/webarch/conf/apache* as above, then rebuild the apache config files:
buildapache earthin buildapache movie buildapache movie_ssl buildapache moviedev buildapache recon buildapache recondev buildapache tc buildapache ts buildapache ttt
And we still have A- "The server does not support Forward Secrecy with the reference browsers." at https://www.ssllabs.com/ssltest/analyze.html?d=parrot.transitionnetwork.org
So edit /etc/apache2/mods-available/ssl.conf:
#SSLProtocol all -SSLv2 SSLProtocol -ALL +SSLv3 +TLSv1 +TLSv1.1 +TLSv1.2
And restart apache and it's still A-.
Perhaps it's because of old openssl libs on the server?
aptitude install deborphan deborphan libssl0.9.8 lynx libdb4.8 libboost-iostreams1.42.0 aptitude remove libssl0.9.8
That didn't help, tried copying the ciphers from wiki:PenguinServer Nginx config:
SSLCipherSuite EECDH+ECDSA+AESGCM:EECDH+aRSA+AESGCM:EECDH+ECDSA+SHA384:EECDH+ECDSA+SHA256:EECDH+aRSA+SHA384:EECDH+aRSA+SHA256:EECDH+aRSA+RC4:EECDH:EDH+aRSA:RC4:!aNULL:!eNULL:!LOW:!3DES:!MD5:!EXP:!PSK:!SRP:!DSS:+RC4:RC4
But it's still a A- and there is this, which is worse:
- IE 11 / Win 8.1 R Protocol or cipher suite mismatch
So reverting to the config from https://github.com/t2d/wasuptls/blob/master/apache-vhost.conf
SSLCipherSuite ECDH+AESGCM:DH+AESGCM:ECDH+AES256:DH+AES256:ECDH+AES128:DH+AES:ECDH+3DES:DH+3DES:RSA+AES:RSA+3DES:!ADH:!AECDH:!MD5:!DSS:!aNULL
This is in any case not a big deal as ticket:540 is outstanding.
- Update wiki:SecurityInfo
All the steps on this page have been reproduced and fingerprints etc updated.
Done.
- Update wiki:DomainNames
Have updated the wiki:DomainNames#transitionnetwork.org section but nothing else on that page.
- Fix Sam's Trac email address
Sam, the address in Trac is this (note the extra dot):
- sam.rossiter@…
You need to change this via the preferences page.
comment:9 Changed 3 years ago by chris
- Add Hours to Ticket changed from 0.0 to 0.25
- Total Hours changed from 3.2 to 3.45
So, we don't want to have half a day next year with an expired certificate, there is a package for this, http://packages.debian.org/wheezy/ssl-cert-check so on wiki:PenguinServer:
aptitude install ssl-cert-check
Find the config files by listing the files that have just been installed:
dpkg -L ssl-cert-check /. /usr /usr/share /usr/share/doc /usr/share/doc/ssl-cert-check /usr/share/doc/ssl-cert-check/copyright /usr/share/doc/ssl-cert-check/changelog.Debian.gz /usr/bin /usr/bin/ssl-cert-check
So, following the suggestion here http://howto.biapy.com/en/debian-gnu-linux/servers/http/setup-an-email-alert-on-ssl-tls-certificate-expiration the following cron job was set up to to check the cert every day:
30 09 * * * ssl-cert-check -qac "/etc/ssl/transitionnetwork.org/transitionnetwork.org.crt" -e "chris@webarchitects.co.uk"
comment:10 Changed 3 years ago by chris
- Add Hours to Ticket changed from 0.0 to 0.2
- Total Hours changed from 3.45 to 3.65
The cronjob was tested on the old cert:
ssl-cert-check -qac "/etc/ssl/transitionnetwork.org/2013/transitionnetwork.org.crt" -e "chris@webarchitects.co.uk"
And the follwing email was sent:
From: root@penguin.webarch.net (root) Date: Sat, 25 Jan 2014 18:06:46 +0000 To: chris@webarchitects.co.uk Subject: Certificate for FILE "(CN: *.transitionnetwork.org)" has expired! The SSL certificate for FILE "(CN: *.transitionnetwork.org)" has expired!
So it works and we should get advanced warning next year.
comment:11 Changed 3 years ago by chris
- Status changed from accepted to closed
- Resolution set to fixed
Closing as this is resolved.

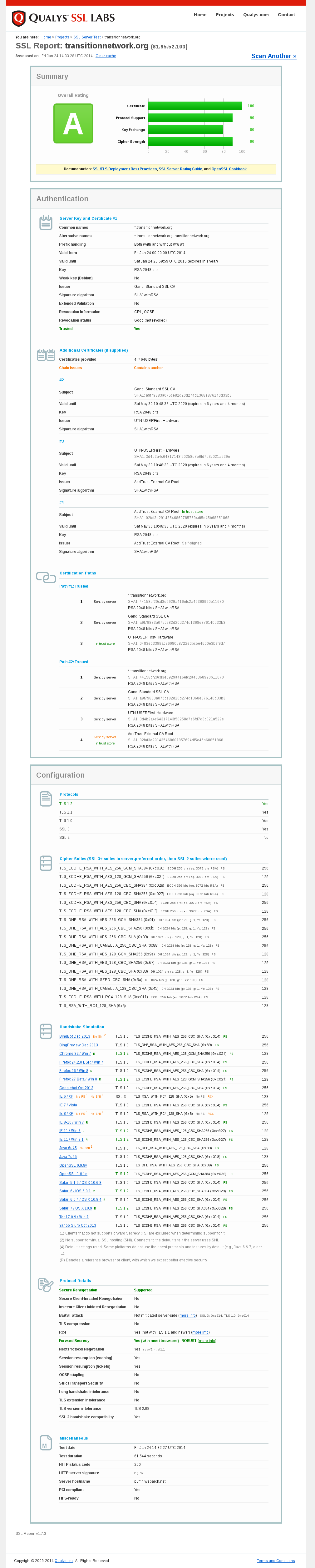
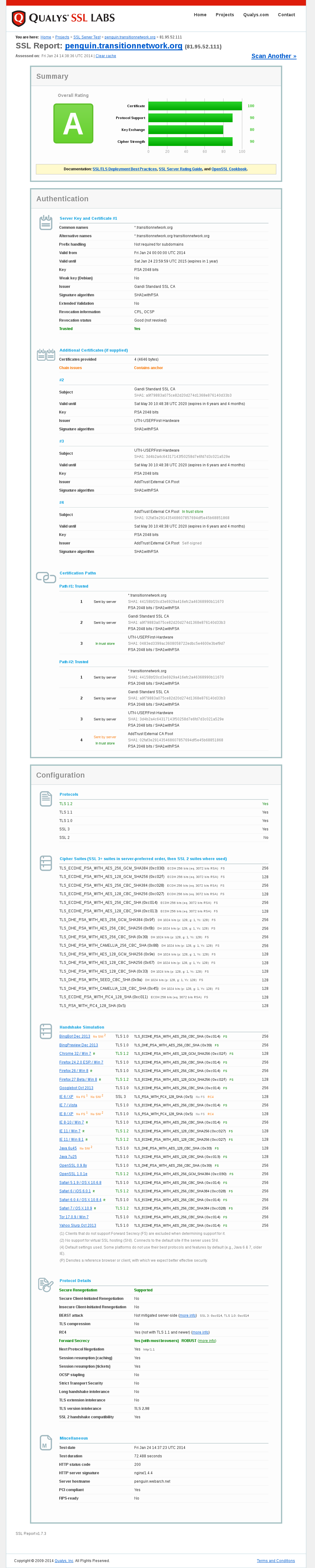
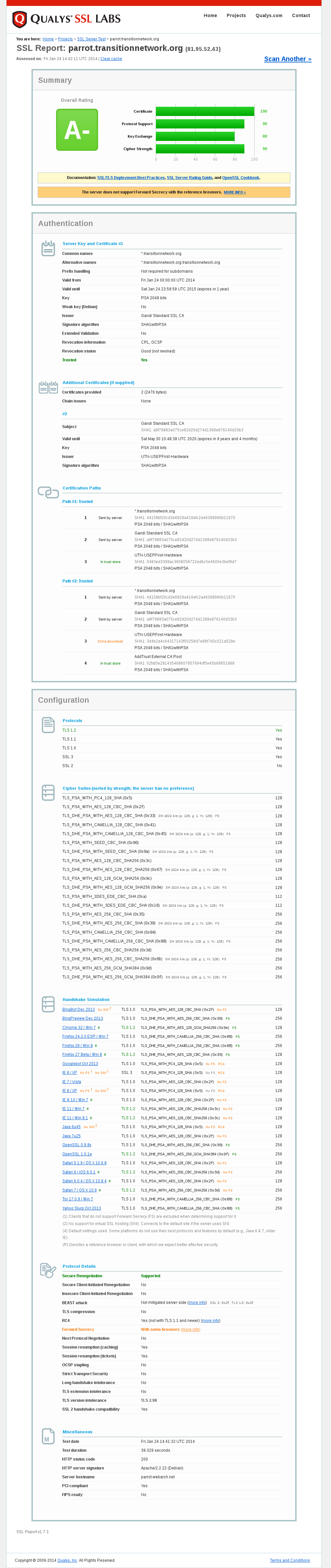
So sorry I missed this yesterday, yes we need to renew it / get a a new one, I'm on the case now.
The quickest way to do it is probably for Webarchitects to buy it and then invoice the Transition Network for it, is that OK? Or do you want to buy it directly?